VoIP Network Security
Harness the Power of Cloud Communications Security
INDUSTRY-LEADING SECURITY & COMPLIANCE
Cloud communication providers may offer similar services that seem the same. The reality is many don't provide the same level of security and compliance businesses should expect from a cloud provider. In this time of constant attacks and ransomware events, your organization must determine if your provider meets the leading industry requirements for compliance and security.
We've implemented the industry's highest compliance and security standards to protect our customers, including achieving HIPAA and PCI-DSS compliance.
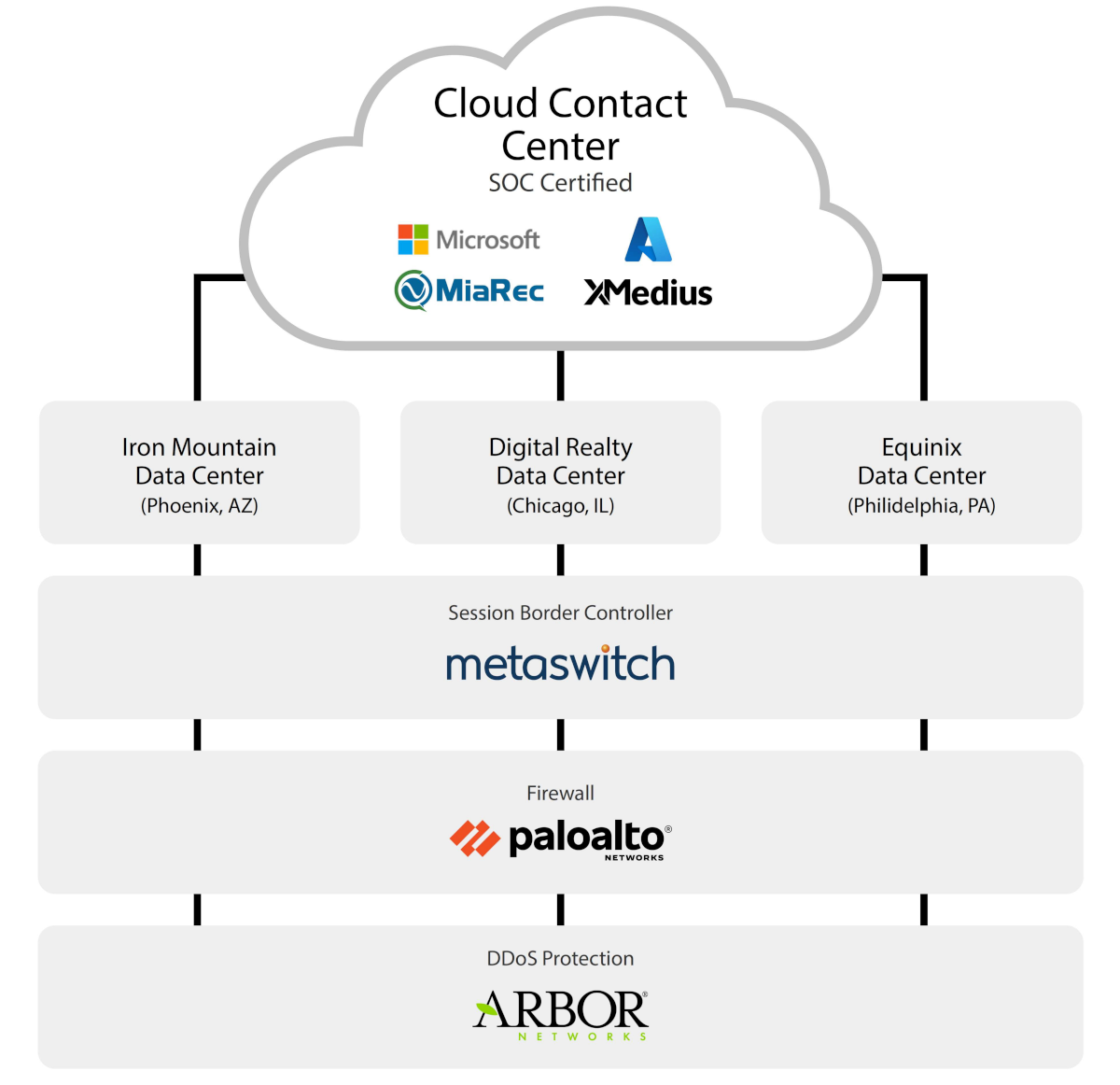
HOW WE SECURE OUR NETWORK & YOUR DATA
METASWITCH NETWORKS PERIMETA SBC
- It's configured to blxk fraudulent SIP User agents at the edge.
- Perimeta reduces our vulnerability to DoS attacks by identifying and as they occur.
- Perimeta uses dynamic denylisting to protect itself and the core network trom attacks.
- Deployed in Geo-redundant configuration.
- Perimeta can blacklist a source for any one of several reasons.
- You can configure different behavior for different reasons, such as exceeding capacity limits, registration message limits, etc.
NETSCOUT ARBOR DDOS PROTECTION
- Best-in-class DDoS Protection
- Inline Physical Security Appliances at the edge of our network
- Automatic Detection & Mitigation
- Protect against multiple attack types:
- DDOS (Distributed Denial Of Service)
- Rotnpts/Ransomware/Command R Control
- Location & Reputation Based Threats
WEB APPLICATION FIREWALL
- Web Application Firewall (WAF) is a cloud-based firewall that helps protect our web applications or APIs against common web exploits and that may affect availability, compromise security, or consume excessive resources.
- Traffic destined for our Cloud applications pass through the WAF.
- Protects our cloud-based applications, including Hosted Fax & Call Recording.
CLOUDFLARE MAGIC TRANSIT DDOS PROTECTION
- Cloud-based DDoS protection for volumetric attacks that would otherwise overwhelm upstream connections.
- Cloudflare Advertises our networks to their data center via BGP in the event Of an attack, sending Clean traffic using aprivate GRE tunnel.
- Capacity to handle up to 37Tbps+ attacks.
PALO ALTO NEXT-GEN FIREWALLS
- Among the highest-rated firewalls in the industry
- State-of-the-art firewalls that protect our corporate network & data center locations.
- Protects applications such as CommPortaI & MetaView Web.
- Constant Threat feed updates equip the firewall with the latest threat prevention and intelligence.
THOUSANDEYES NETWORK VISBILITY
- Provides network visibility through thousands of global monitoring vantage points across the Internet and within our own network
- Simulates user interactions on web-based applications and sites
- Provides a global Internet weather map, showing real-time and historic network operational and outage status from ISPs across thc world
CUSTOM FRAUD APPLICATIONS
- Toll Fraud Detection - Detects suspicious calls and automatically blocks international calling.
- Domestic Toll Detection and mitigation - Detects suspected traffic based on cost and alerts us to the activity.
- SIP Brute Force Attack Detection - Detects Suspicious activity to our SIP provisioning server and blocks the IP address in our Arbor Appliances.
- CommPortal Brute Force Attack Detection - Detects suspicious activity and blocks the offending IP address in our Arbor Appliances
REDSHIFT NETWORKS
- Redshift Networks is an industry leader in carrier-grade VoIP/SlP security, threat intelligence analytics and Fraud-detection technology.
- Detects and alerts the presence of malicious SIP User Agents.
- Provides cost-based call analytics used to identify calls to high-cost areas.
- Provides visibility to misconfigured endVY)ints sending Subscribe Messages and Notify Messages.
- Provides historical call history and search capabilities.
SECURITY OPERATIONS CENTER (SOC) COMPLIANCE & SECURITY
Our network is SOC-certified and geo-redundant through our Phoenix, Chicago and Philadelphia data centers.
Call Fraud Detection

SIP
Analytics
DDoS
Protection

Network
Visibility

